

How Age Verification Is Eating the Internet
Remember the internet before the ID checks, biometric scans, and “prove-you’re-over-18” pop-ups? Yeah, me neither.
What used to be a place for memes, chaos, and unfiltered creativity is now fast turning into a high-tech playground where every click, every swipe, and every login is being watched, logged, and verified. And let’s be real: this isn’t just about “protecting kids” or “keeping content safe.”
This is a full-on land grab of our digital anonymity, packaged in a warm, emotional wrapper so convincing you won’t even notice until it’s too late.
Safety Tech: The Internet’s New Bouncers
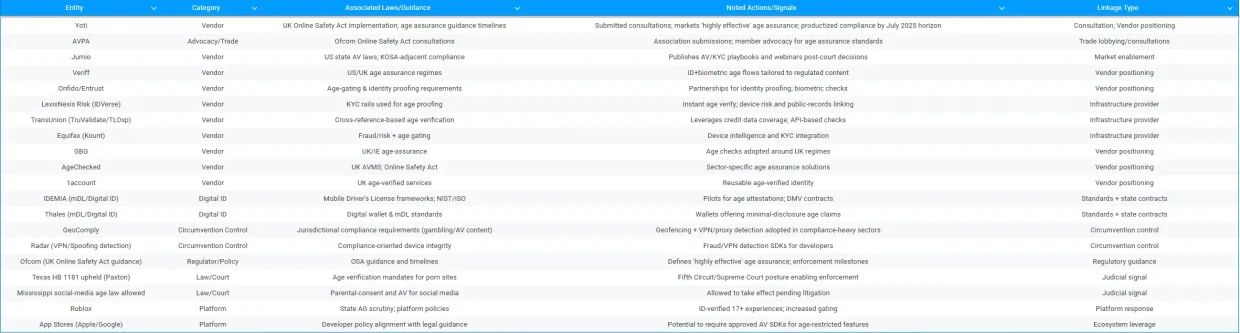
Meet the new gatekeepers: companies like Yoti, Jumio, Veriff, Onfido, and Entrust. These are the digital bouncers of the internet, checking IDs, scanning faces, and even analyzing your biometrics.
Want to watch a cat video that’s “age-restricted”? Better be ready to hand over your data.
Take Yoti, for example. They’ve been publicly aligning their services with Ofcom’s Online Safety Act, gearing up for the July 2025 compliance deadline in the UK.
Their pitch? “Highly effective age assurance.”
Translation: scan your ID, submit a selfie, and voilà – you’re allowed to browse. The kicker is that these companies profit for verifications and, once embedded into platforms, create an almost impenetrable moat for competitors.
Data Brokers: The Silent Watchers
Even if you dodge the selfie check, data brokers like Equifax (via Kount) and TransUnion (via TruValidate) are already cross-referencing your name, address, and birthdate behind the scenes.
They call it “identity proofing” or “age verification,” but we call it creepy omnipresence.
These aren’t small-time operations. They’re giant, decades-old surveillance networks, now repurposed for age verification. Every verification request adds to their data leverage, turning the entire internet into their compliance playground.
Digital ID Wallets: Your Privacy in a Wallet App
If you thought mobile wallets were just for paying for overpriced coffee, think again. IDEMIA and Thales are pushing digital ID wallets and mobile driver’s licenses, which claim to “minimally disclose” age while proving identity.
Convenient? Sure. Dangerous? Absolutely.
If these tools become the standard, your anonymity is gone. Every age-checkable interaction – gaming, shopping, streaming – is now a potential surveillance point, all neatly logged in your phone’s digital wallet.
VPN & Proxy Detection: The Death of Escape Routes
Platforms & App Stores: The Meta-Winners
Big tech companies love this.
Apple, Google, Microsoft – hell, they already own the gates. Once regulators say “here’s the approved method,” platforms just fold it into developer requirements.
Developers comply or die (on the app store charts). Suddenly, every app you use is part of this verification ecosystem.
Advocacy & Emotional Manipulation
Here’s where it gets sneaky though.
Organizations like Common Sense Media and 5Rights aren’t selling data – they’re selling emotional leverage. By framing verification as a fight to “protect the kids,” they manufacture public outcry. Enough noise, and politicians and regulators push mandatory policies in the name of kids’ safety.
This is emotional engineering, plain and simple. Once people consent to verification in the name of protection, rolling back becomes nearly impossible and the internet as we know it will be gone forever.
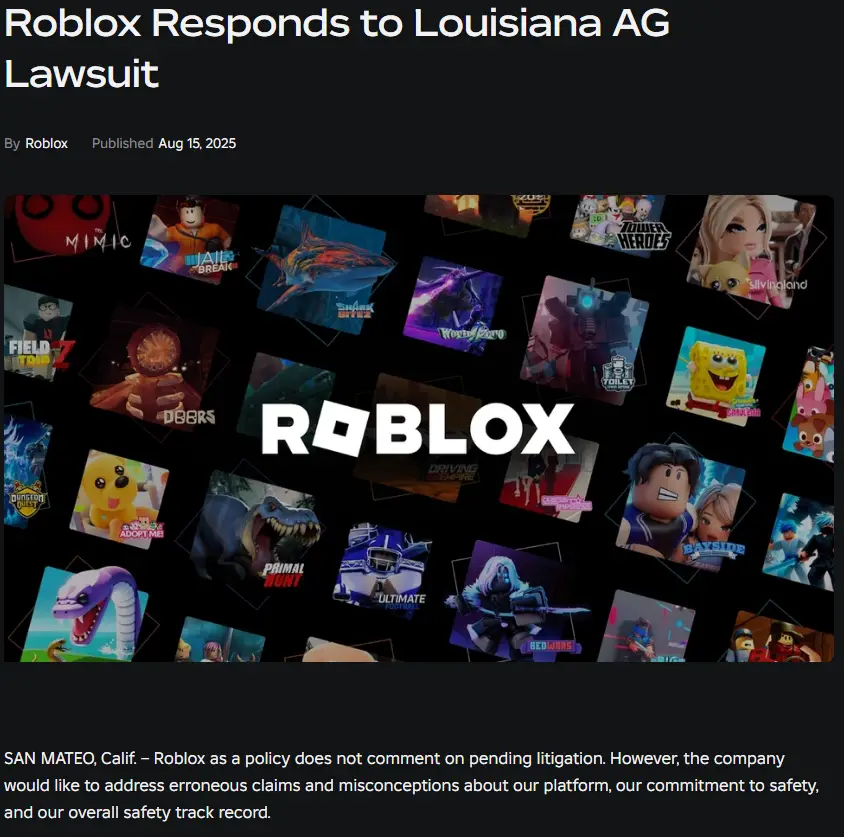
Roblox: The Case Study We All Saw Coming
Roblox, the gaming platform beloved by kids and teens, got hit with lawsuits over alleged inadequate child safety protections.
In response, Roblox rolled out video selfie verification and government ID checks. It’s “safety” on paper, but in practice, it’s another biometric data pool feeding into corporate and regulatory systems.
And now, even innocent Roblox gameplay is apparently a surveillance vector.
The Feedback Loop of Evil: How the System Locks In
Advocacy groups push emotional narratives.
Regulators consult vendors and NGOs.
Laws name “effective” verification methods.
Platforms integrate approved systems.
Vendors profit and lobby for the next wave.
Every loop tightens the grip on online anonymity. Every verification cycle increases the stakes. Every platform update locks the internet a little tighter.
How We Fight Back to Keep Our Digital Privacy Free
You want to keep using the internet like a free human being? Here’s the playbook:
Speak up: Comment on public consultations, advocate for privacy-friendly alternatives.
Use tech that protects you: VPNs, encrypted messaging, privacy browsers.
Support civil-liberty groups: The EFF, National Coalition Against Censorship, and others need funding and vocal support to push back.
Stay informed: Awareness is your first defense. Policies sneak in fast and silence only helps them.
Remember, this isn’t about panic – it’s about choice. Anonymity and privacy are only worth something if we actively defend them.
Defend Your Rights While You Can Before It's Too Late
The internet is under siege by a mix of tech vendors, data brokers, advocacy groups, and platforms, all working in parallel to make age verification and surveillance mandatory.
Emotional manipulation gets the public on board, legal changes force compliance, and the result is a tracked, monitored, and far less free web. Everything happening in the U.K. and now with Roblox is giving us a glimpse of the future – and it’s not pretty.
Fight for your digital freedom now, or it might vanish forever.
This was a commentary article based on publicly available information and personal opinion. Readers are encouraged to form their own conclusions based on the sources cited.
All images, logos, and video clips used in this article are the property of their respective owners. This content is used for the purposes of commentary, criticism, and news reporting under the guidelines of Fair Use (17 U.S.C. § 107). No copyright infringement is intended. If you are the copyright holder and believe your content has been used improperly, please contact us directly.
Want More?
Check These Out Next!
About Report AFK
A place for gamers, by gamers, untarnished by corporate gaming media and their nonstop attempts to elevate bad games while denouncing any developers brave enough to stand up to them.
Site Links
Copyright 2026 ReportAFK.com









Mike R
August 17, 2025
Preach! I been talking about this stuff for years and they just keep trying. Need to scream it from thr mountains!
Ayefkay
August 18, 2025
Hey Mike, thanks for stopping by and I’m glad you liked the article!
Tyler W
August 21, 2025
I saw Hypnotic talk about this on stream a week or so ago and it sounds pretty fcked up ngl
Ayefkay
August 22, 2025
Hey Tyler, thanks for stopping by and it definitely is. I try to make it to Hypno streams too so maybe I’ll see you around in there!